In today’s fast-evolving technological landscape, digital transformation is no longer optional but a necessity for organizations striving to remain competitive, secure, and efficient. The transformation journey, however, is complex, demanding a strategic approach that balances innovation with governance, risk management, and operational excellence.
This article explores the transformation journey from the perspective of an accomplished IT Infrastructure and Security leader with over 14 years of experience across banking, telecom, and healthcare sectors. His journey reflects the quintessential roadmap many organizations must navigate to achieve sustainable success in the digital era.
Starting Point: Legacy Systems and Operational Challenges
Early in his career as a network and system administrator, the leader dealt with the realities of legacy infrastructure—outdated hardware, siloed operations, and manual processes that limited agility and scalability. Challenges included:
- Maintaining high availability and uptime amid growing demand
- Managing security risks with limited frameworks in place
- Coordinating complex network configurations across diverse environments
- Handling compliance with emerging regulatory standards
These initial challenges laid the foundation for a deep understanding of the operational and security risks organizations face during digital transitions.
Embracing Cloud and Automation: Catalysts for Change
As the transformation journey progressed into leadership roles, the focus shifted toward cloud adoption and automation:
- Cloud Migration: Transitioning critical workloads to cloud environments (AWS, Azure, Oracle Cloud) reduced operational costs by up to 30%, while significantly improving system scalability and reliability.
- Automation of CI/CD Pipelines: By automating deployment processes using tools like Jenkins, Docker, Kubernetes, and cloud-native services, deployment times shrank by 40%, accelerating time-to-market.
- Agile Methodologies: Implementing Agile project management increased team efficiency by 20%, fostering better collaboration and faster delivery cycles.
These changes reflected a paradigm shift—from rigid, manual processes to flexible, cloud-native, and automated infrastructure.
Strengthening Cybersecurity and Risk Posture
Digital transformation cannot succeed without robust cybersecurity and risk management. This leader’s certifications (CISA, CISM, CRISC, CCISO) underpin his ability to design and implement comprehensive security frameworks aligned with ISO 27001, NIST, and other global standards. Key initiatives included:
- Developing an Information Security Management System (ISMS) that improved compliance and reduced vulnerabilities by 30%.
- Establishing Business Continuity and Disaster Recovery plans that lowered operational risks by 40%.
- Integrating real-time monitoring and machine learning analytics to boost infrastructure visibility and proactive threat detection by over 35%.
These measures ensured transformation efforts did not compromise security or compliance but rather strengthened the organization’s risk posture.
Leadership: Bridging IT and Business Strategy
True transformation extends beyond technology—it demands leadership that aligns IT capabilities with business goals. Leading teams of 20+ professionals, this leader demonstrated:
- Effective stakeholder engagement, driving a 25% improvement in client satisfaction
- Strategic vendor management, optimizing costs without sacrificing quality
- Fostering a culture of accountability, innovation, and continuous improvement
His ability to translate complex technical initiatives into clear business value helped bridge gaps between IT and business units, creating a unified transformation vision.
Lessons From the Transformation Journey
- Start with a Clear Strategy: Transformation begins with understanding business objectives and aligning technology initiatives accordingly.
- Prioritize Security from Day One: Embedding cybersecurity into every phase of transformation prevents costly breaches and compliance failures.
- Empower People and Processes: Technology is only as effective as the people who operate it; investing in skills and agile processes pays dividends.
- Measure and Adapt: Continuous monitoring, risk assessment, and process refinement are critical to sustain transformation benefits.
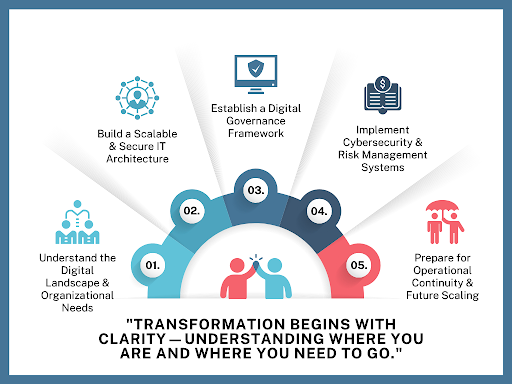
Conclusion: Transformation as a Continuous Journey
The journey of IT infrastructure and security transformation is ongoing. It requires visionary leadership, technical acumen, and an unrelenting focus on aligning technology with business goals. The experience shared here reflects how organizations can successfully navigate digital disruption by embracing cloud innovation, strengthening cybersecurity, and leading with purpose.
“Transformation is not just about technology—it’s about empowering people and processes to create lasting value.”
For any organization embarking on or accelerating their digital transformation, these insights offer a roadmap to sustainable success.













